AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Authenticity PowerPoint Presentation Templates and Google Slides
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 78 Item(s)
Page
Slide 1 of 12
Improve your presentation delivery using this software authentication cloud icon flowchart ppt powerpoint presentation complete deck. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.







Slide 1 of 7
This is a two factor authentication example of ppt presentation. This is a two stage process. The stages in this process are something you know, something you have.







Slide 1 of 7
This is a authentic leadership powerpoint slides information. This is a six stage process. The stages in this process are authentic leadership, relational leadership model, emotionally intelligent leadership, servant leadership, leadership practices inventory, transformational leadership.







Slide 1 of 7
This is a leadership and authenticity ppt presentation. This is a four stage process. The stages in this process are outdoor activity day, personal leadership challenges, authentic leadership, leadership and authenticity.







Slide 1 of 7
This is a identification and authentication powerpoint slide deck. This is a four stage process. The stages in this process are incident response, identification and authentication, access control, digital signature management.






Slide 1 of 6
This is a authentic american food burger logo stamp design ppt powerpoint presentation file elements. This is a four stage process. The stages in this process are american cuisine, american meal, american food.






Slide 1 of 6
This is a authentic american cuisine stamp sign logo ppt powerpoint presentation file graphics template. This is a three stage process. The stages in this process are american cuisine, american meal, american food.
Slide 1 of 5
This is a safety and authentication vector icon ppt powerpoint presentation model rules. This is a one stage process. The stages in this process are password, access approval, authentication icon.
Slide 1 of 5
This is a laptop with lock password authentication vector icon ppt powerpoint presentation icon summary. This is a one stage process. The stages in this process are password, access approval, authentication icon.




Slide 1 of 4
This is a authentic content free platform ppt slides. This is a four stage process. The stages in this process are design, success, business.


Slide 1 of 2
Presenting 7 stage pyramid infographics for authentication system ppt powerpoint presentation file good pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including 7 stage pyramid infographics for authentication system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


Slide 1 of 2
Persuade your audience using this 7 petal diagram for cloud access with secure authentication ppt powerpoint presentation file designs pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including 7 petal diagram for cloud access with secure authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Pitch your topic with ease and precision using this work space authentication process flow of verification factors icons pdf. This layout presents information on rust relationship, authentication, corporate data center. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


Slide 1 of 2
Persuade your audience using this user authentication process flow of verification factors for smart phone authorization rules pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including additional authentication credential required, send authentication request with session and passcode, response returns with token . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Showcasing this set of slides titled customer authentication process flow of verification factors for safe access vector icon infographics pdf. The topics addressed in these templates are customer authentication process flow of verification factors for safe access vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
Persuade your audience using this collaborative authentication process flow of verification factors slides pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including authentication required for user, enter passcode, secondary authentication process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
Presenting authentication process flow of verification factors interface authentication template pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including enter interface credentials, login successful, application push notification approval. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


Slide 1 of 2
Pitch your topic with ease and precision using thisauthentication process flow of verification factors from client and server side structure pdf This layout presents information on individual enters password, second form of authentication, one time password entered manually. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Slide 1 of 2
Persuade your audience using this authentication process flow of verification factors for user profile authentication icon portrait pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including authentication process flow of verification factors for user profile authentication icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
Pitch your topic with ease and precision using this authentication process flow of verification factors for user application rules pdf. This layout presents information on password authentication, code authentication, user passcode login. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


Slide 1 of 2
Showcasing this set of slides titled authentication process flow of verification factors for server infographics pdf. The topics addressed in these templates are authentication server or customer server,authentication verified by server system, response with verification results. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Slide 1 of 2
Presenting data quality vector showing authentication document icon ppt powerpoint presentation gallery tips pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including data quality vector showing authentication document icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


Slide 1 of 2
Presenting bank note with watermark authentication stamp ppt powerpoint presentation example 2015 pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including bank note with watermark authentication stamp. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Slide 1 of 2
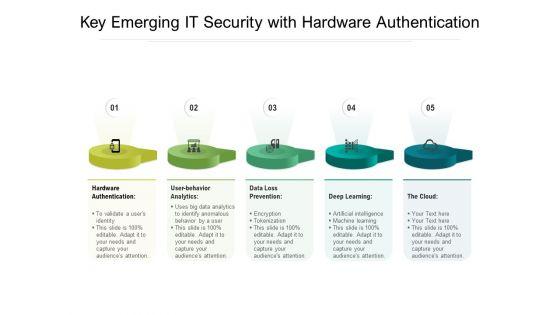
Persuade your audience using this key emerging it security with hardware authentication ppt powerpoint presentation gallery file formats pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including hardware authentication, user behavior analytics, data loss prevention, deep learning, the cloud. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
Pitch your topic with ease and precision using this server room layout vector with authentication ppt powerpoint presentation gallery pictures pdf. This layout presents information on server room layout vector with authentication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


Slide 1 of 2
Presenting this set of slides with name biometric authentication for customer verification ppt powerpoint presentation slides smartart pdf. This is a three stage process. The stages in this process are biometric authentication for customer verification. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name android fingerprint authentication with mobile user ppt powerpoint presentation visual aids inspiration pdf. This is a three stage process. The stages in this process are android fingerprint authentication with mobile user. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name authentication techniques ppt powerpoint presentation professional themes cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like authentication techniques to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name behavioral biometrics authentication ppt powerpoint presentation outline design ideas cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like behavioral biometrics authentication to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name access control authentication ppt powerpoint presentation images cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like access control authentication to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name authentication information security ppt powerpoint presentation ideas guide cpb pdf. This is an editable Powerpoint seven stages graphic that deals with topics like authentication information security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name smart card authentication ppt powerpoint presentation infographics slides cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like smart card authentication to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name credit card authentication ppt powerpoint presentation model cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like credit card authentication to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name two factor authentication api ppt powerpoint presentation professional templates cpb. This is an editable Powerpoint two stages graphic that deals with topics like two factor authentication api to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name captive portal authentication ppt powerpoint presentation slides graphics design cpb. This is an editable Powerpoint five stages graphic that deals with topics like captive portal authentication to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name two factor authentication ppt powerpoint presentation slides diagrams cpb. This is an editable Powerpoint four stages graphic that deals with topics like two factor authentication to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name identity management authentication ppt powerpoint presentation inspiration structure cpb. This is an editable Powerpoint six stages graphic that deals with topics like identity management authentication to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name api authentication authorization ppt powerpoint presentation summary demonstration cpb. This is an editable Powerpoint six stages graphic that deals with topics like api authentication authorization to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.


Slide 1 of 2
Presenting this set of slides with name authentication server ppt powerpoint presentation outline layouts cpb. This is an editable Powerpoint nine stages graphic that deals with topics like authentication server to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.









Slide 1 of 9
This slide provides the use of multiple authentication and authorization technology which are used to protect systems and user information. Key categories are password based, multi factor, certificate based, biometrics and token based. Persuade your audience using this User Authentication And Authorization Security Management Technology Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Based, Multi Factor, Certificate Based, Biometrics, Token Based. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.









Slide 1 of 9
This slide showcases the different types of digital certificate for internet authentication. It includes types such as domain-validated SSL, organization and extended validation SSL and client certificates. Presenting Categories Of Online Certificate For Internet Authentication Ppt Portfolio Samples PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Domain Validated SSL, Organization Validated SSL, Extended Validation SSL. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.









Slide 1 of 9
Pitch your topic with ease and precision using this Italian Food Dishes Authentic Dish Palo Risotto Clipart PDF. This layout presents information on Italian Food Dishes, Authentic Dish Palo Risotto. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Slide 1 of 1
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Explore a selection of the finest Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Two Factor Authentication Process Flow For Enhanced Security Ppt Gallery Graphic Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.


Slide 1 of 2
Persuade your audience using this business objective presentation graphics of token based authentication mockup pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including business objective presentation graphics of token based authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.





































































Slide 1 of 69
While your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Implementing Authentication In Application Security PPT Example deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, its downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck. Our Implementing Authentication In Application Security PPT Example are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.









Slide 1 of 9
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.









Slide 1 of 9
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Complete Beginners Guide Two Factor Authentication For Improved Security Fin SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Complete Beginners Guide Two Factor Authentication For Improved Security Fin SS V today and make your presentation stand out from the rest This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.









Slide 1 of 9
This slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc. This modern and well-arranged Difference Between Authentication And Authorization Application Security Testing provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide showcase the difference between authentication and authorization in application security on aspects such as purpose, operation, etc.









Slide 1 of 9
This slide discusses about the overview of authentication in application security and the various elements of MFA. Present like a pro with Authentication In Application Security For Data Protection Application Security Testing. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide discusses about the overview of authentication in application security and the various elements of MFA.









Slide 1 of 9
This slide highlights the concept of smart contracts used for cybersecurity authentication and its use cases. It includes access control in shared spaces, identity verification, supply chain authentication and medical record access. This Visionary Guide To Blockchain Using Smart Contracts For Authentication BCT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Visionary Guide To Blockchain Using Smart Contracts For Authentication BCT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide highlights the concept of smart contracts used for cybersecurity authentication and its use cases. It includes access control in shared spaces, identity verification, supply chain authentication and medical record access.









Slide 1 of 9
This slide showcases integration of biometrics powered digital onboarding process which helps in improving convenience and provides better security. It provides information regarding account opening, survey, know your customer and access control. Take your projects to the next level with our ultimate collection of Digital Approach To Client Using Biometric Authentication In Digital Customer Onboarding. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide showcases integration of biometrics powered digital onboarding process which helps in improving convenience and provides better security. It provides information regarding account opening, survey, know your customer and access control.









Slide 1 of 9
This slide highlights various types of biometric authentication technologies used in making services which helps in improving data identification processes. It provides information regarding fingerprint sensor, voice recognition, iris identification and facial recognition. Presenting this PowerPoint presentation, titled Digital Approach To Client Types Of Biometric Authentication Methods Used In Banking, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Digital Approach To Client Types Of Biometric Authentication Methods Used In Banking. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Digital Approach To Client Types Of Biometric Authentication Methods Used In Banking that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide highlights various types of biometric authentication technologies used in making services which helps in improving data identification processes. It provides information regarding fingerprint sensor, voice recognition, iris identification and facial recognition.









Slide 1 of 9
This slide showcases authentication hub for various data validation method across various banking channels. It includes elements such as fingerprint sensors,voice, facial recognition, iris identification, pin or password etc. Find highly impressive Digital Approach To Client Biometrics Authentication Hub For Bank Customers on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Digital Approach To Client Biometrics Authentication Hub For Bank Customers for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases authentication hub for various data validation method across various banking channels. It includes elements such as fingerprint sensors,voice, facial recognition, iris identification, pin or password etc.









Slide 1 of 9
This slide highlights the concept of smart contracts used for cybersecurity authentication and its use cases. It includes access control in shared spaces, identity verification, supply chain authentication and medical record access. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V This slide highlights the concept of smart contracts used for cybersecurity authentication and its use cases. It includes access control in shared spaces, identity verification, supply chain authentication and medical record access.









Slide 1 of 9
This slide exhibits several IoT device authentication models for secure communication between machines. It includes methods such as digital certificates, hardware security module, trusted platform module and symmetric keys. Boost your pitch with our creative Building Trust With IoT Security Methods For Deploying Strong Device Authentication IoT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide exhibits several IoT device authentication models for secure communication between machines. It includes methods such as digital certificates, hardware security module, trusted platform module and symmetric keys.









Slide 1 of 9
This slide showcases the IoT device authentication overview with types. It includes types such as one way authentication, two way authentication, and three way authentication. Do you know about Slidesgeeks IoT Device Management Fundamentals IoT Device Identification Authentication Types IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide showcases the IoT device authentication overview with types. It includes types such as one way authentication, two way authentication, and three way authentication.









Slide 1 of 9
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.










Slide 1 of 10
This slide outlines the various kinds of two-factors authentication methods. The purpose of this slide is to showcase the two factor authentication types such as SMS, and TOTP. It also includes the benefits and limitation of both.This modern and well-arranged Varieties Of Two Factor Authentication Method Cryptocurrency Management With Blockchain provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide outlines the various kinds of two-factors authentication methods. The purpose of this slide is to showcase the two factor authentication types such as SMS, and TOTP. It also includes the benefits and limitation of both.









Slide 1 of 9
This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.Get a simple yet stunning designed Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.









Slide 1 of 9
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CASB 2 0 IT Cloud Access Security Broker And User Authentication to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0.
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 78 Item(s)
Page
